HAL GTZC Use Cases ¶
Switch from secure application to non-secure application for TZEN=1 ¶
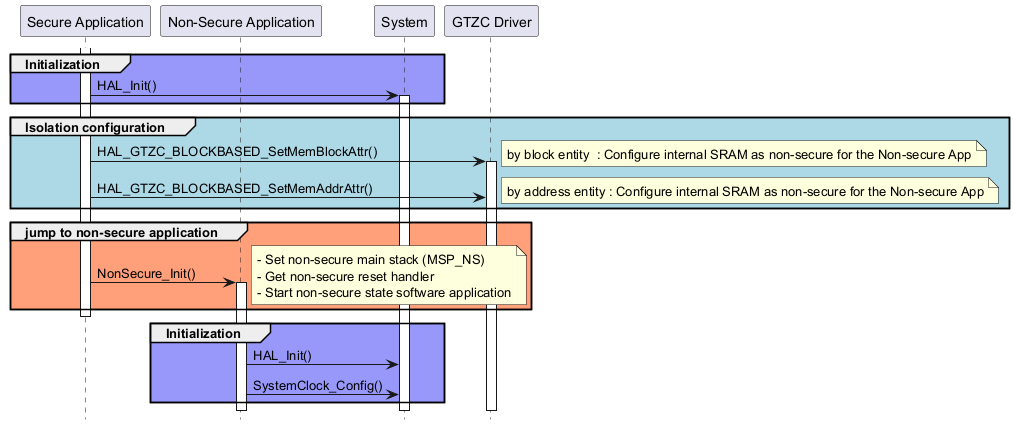
Called functions:
Isolation configuration for TZEN=1 ¶
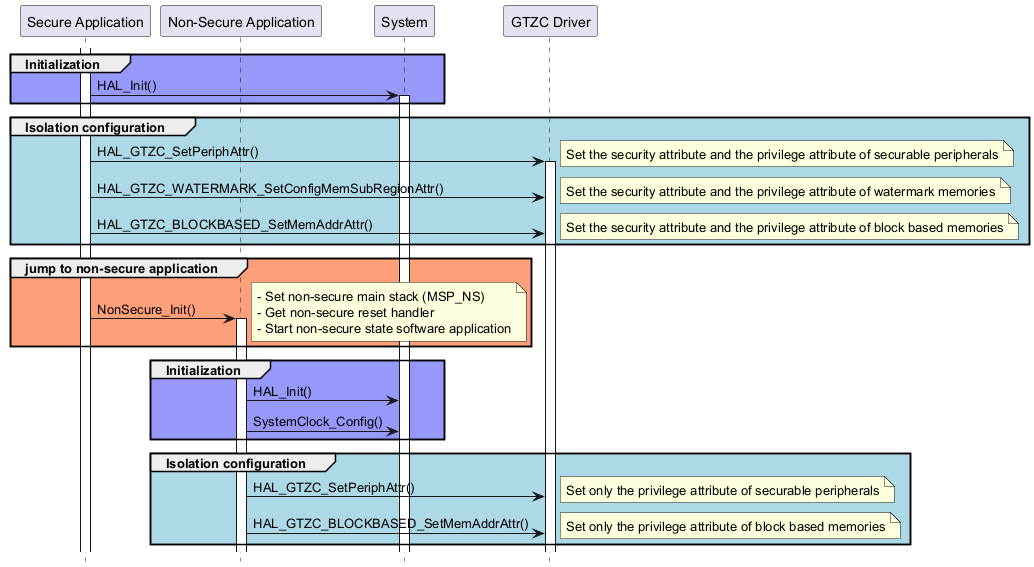
Called functions:
Isolation configuration for TZEN=0 ¶
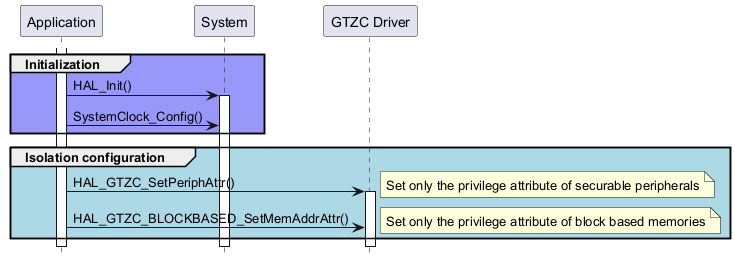
Called functions:
Illegal access interrupt for TZEN=1 ¶
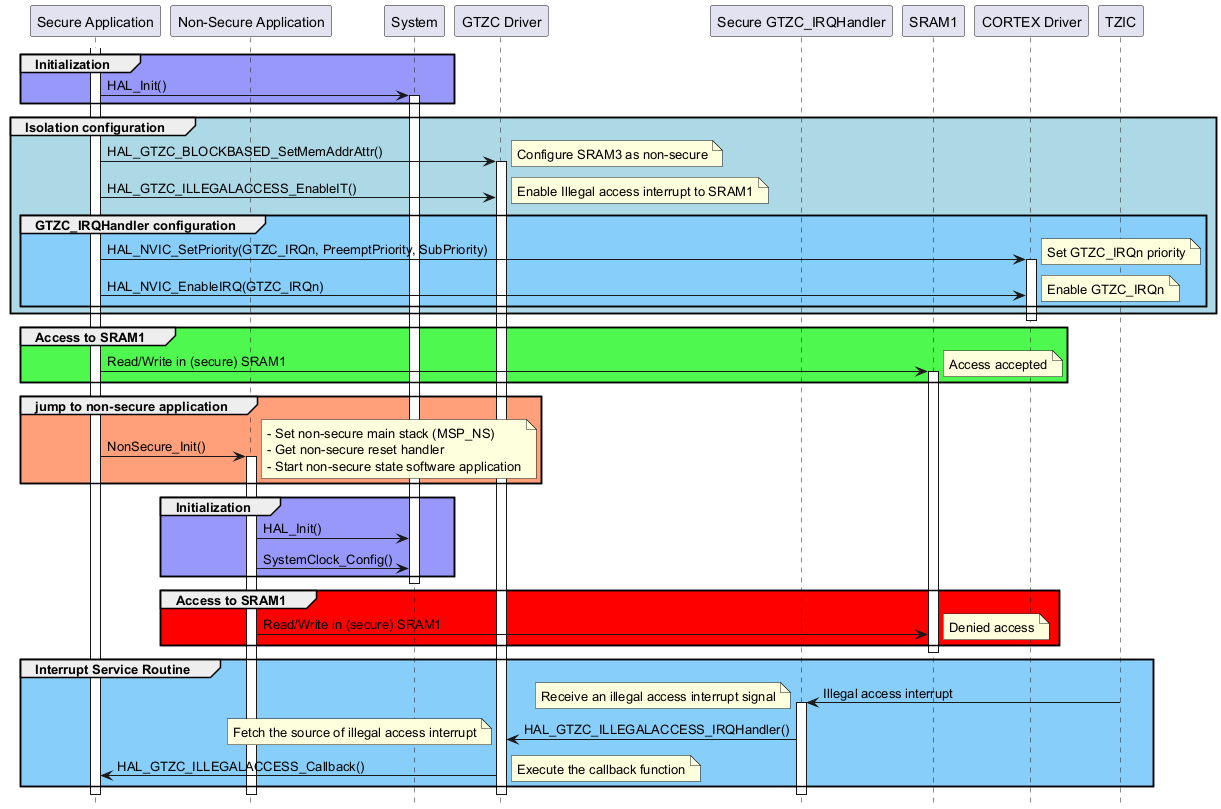
Called functions:
Securable peripherals configuration APIs in secure application ¶
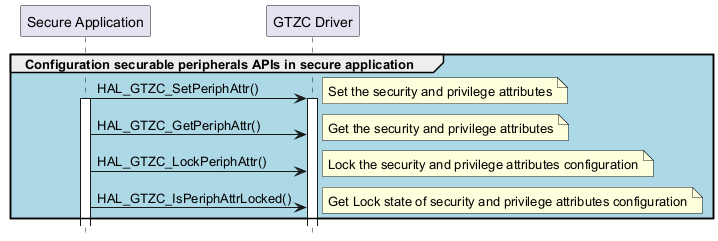
Called functions:
Securable peripherals configuration APIs in non-secure application ¶
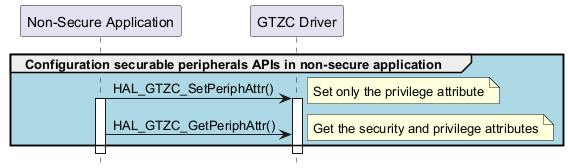
Called functions:
Watermark configuration APIs in secure application ¶
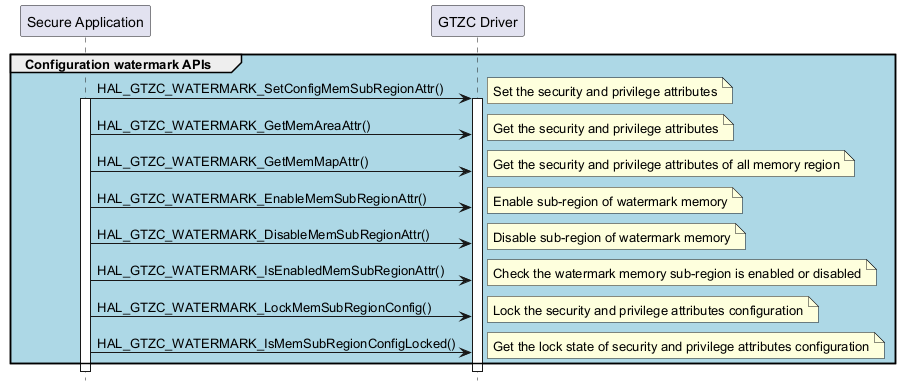
Called functions:
Block based configuration APIs in secure application ¶
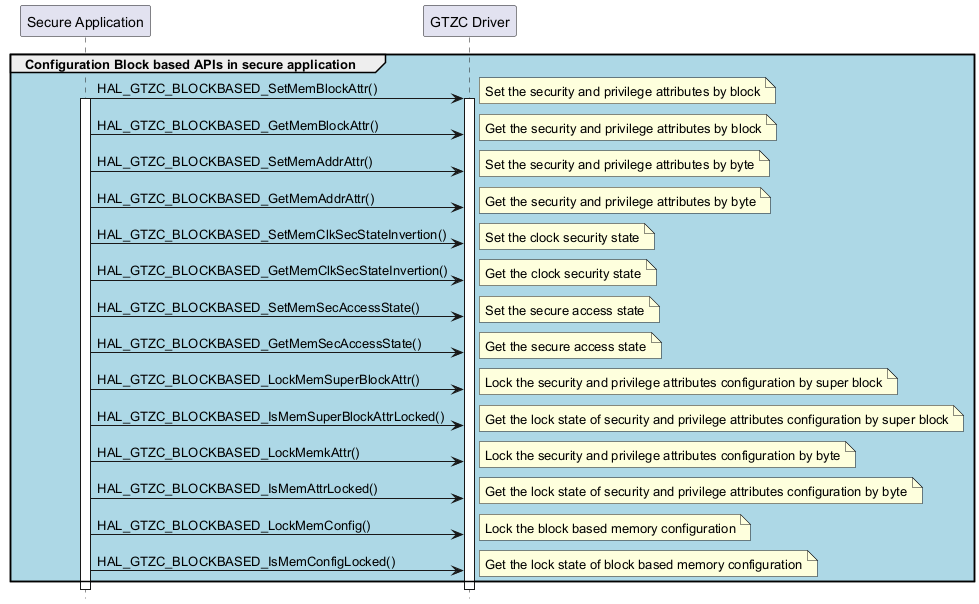
Called functions:
Block based configuration APIs in non-secure application ¶
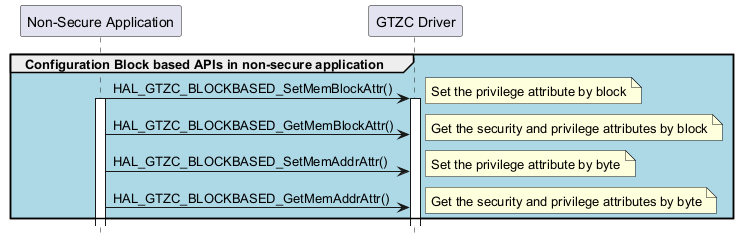
Called functions:
Illegal access configuration APIs in secure application ¶
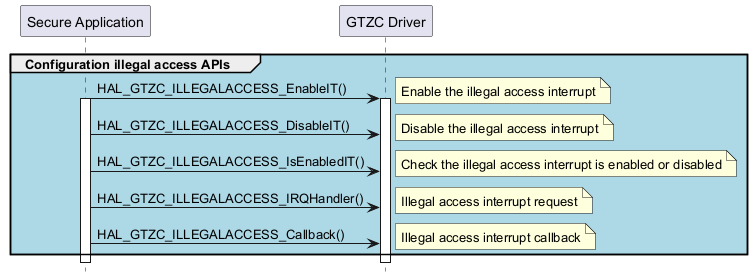
Called functions: